Improving My Ghidra GUI + Ghidra Skills

Hi all, Today I am writitng this post to let you know how i improved My Ghidra GUI & Ghidra Skills. We will be Discussing the below topics
- Customizing Code Browser
- Key Bindings
- Ghidra Extensions
- Ghidra Scripting
Customizing Code Browser
Ghidra CodeBrowser has many Windows which helps in our analysis. My aim was to reduce switchig between Windows as less as possible. So I found the Windows i used the most and Combined them in the Main CodeBrowser Window. The Sections in My CodeBrowser Windows are
- Symbol Tree
- Data Type Manager
- Listing Window
- Function Graph
- Function Call Graph
- Decompiler
- Defined Strings
- Console
- Bookmarks
- Python
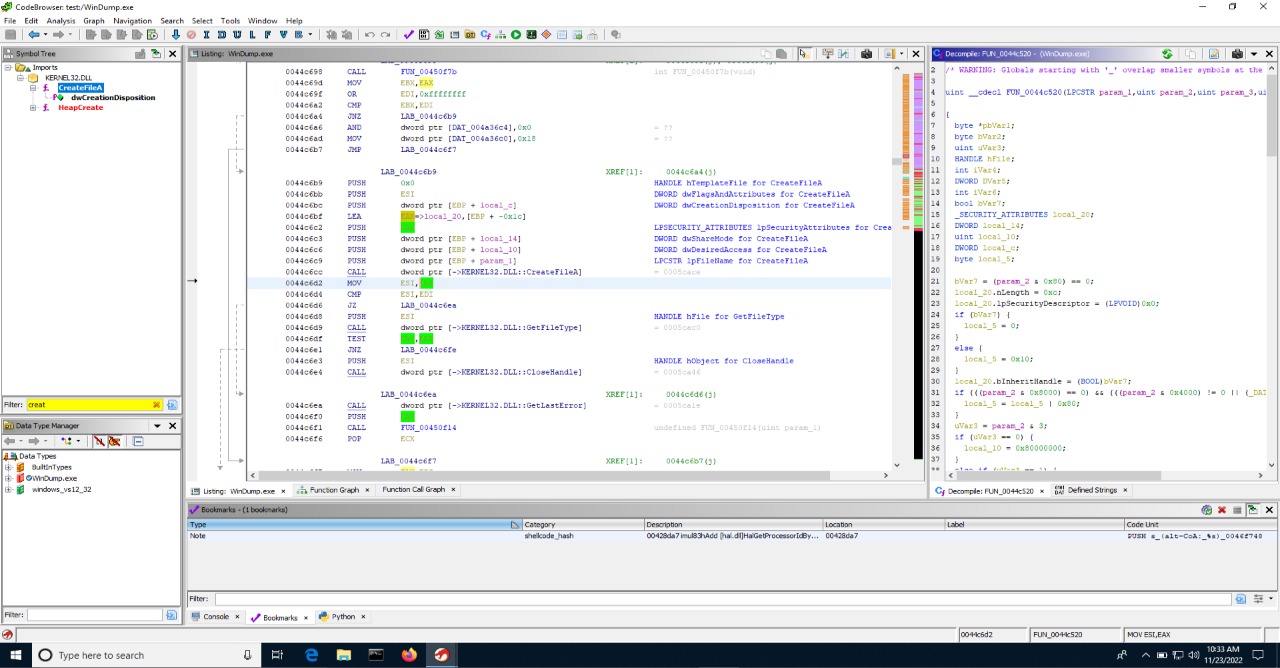
I won’t recommend you to use this Same Sections. Try to find the Windows you use the most and Combine them in the CodeBrowser. You Can add this Windows by Visiting Windows > “Windows you want to View”. After that adjust them by dragging the Windows
Ghidra Lets you Cutomize the Code Browser by Visiting Edit > Tool Options.
An option which helped me a lot is Cursor Text Highlighting:
- Click Edit > Tool Options
- Under Cursor Text Highlight select “Mouse Button to Activate” to “LEFT” (This will highlight the occurence of a selected string in Listing/Decompiler Window)
Key Bindings
Ghidra Key Bindings helps you to perform actions related to Ghidra. Ghidra Has So many default KeyBindings Full List of Key Bindings. Ghidra also help you to add custom Key Bindings by visiting Edit > Tool Options > Key Binding. Here is a list of Key Bindings(Default + Custom) I use the most
- L : Edit Label / Rename Function / Rename Variable
- Ctrl + L : Retype Variable
- T: Choose Data Type
- X: Show Xrefs TO
- Shift + [ = Create Structure
- F3 = Edit Function Signature
- C = Clear Code
- D = Disassemble
Find the actions you perform the Most. look if there is a Key Binding for it. if not add a custom Key Binding. Setting Key Bindings for most used actions is a good practice
Ghidra Extensions
Ghidra Extensions help you to import other features which are not in Ghidra. You can install a Ghidra Extension in GUI by going to Ghidra project Manager Window.
- Click File → Install Extensions
- Click on the ‘+’ icon in the Top right
- Select the folder Which Contain the Ghidra Extension
- After Importing Make sure Box under the Extension you want to install is Checked
- Click OK and Restart Ghidra
Find the Ghidra Documentation for extensions Here .These are the Two Extensions i have found usefull
- Ghidrathon : The FLARE team’s open-source extension to add Python 3 scripting to Ghidra.
- Kaiju : Kaiju is a binary analysis framework extension for the Ghidra software reverse engineering suite
Ghidra Scripting
Ghidra Supports Scripting in multiple languages. I use python for scripting in Ghidra. Ghidra API is very powerfull that we can replace a Multiline code with a single Ghidra API function Call.I will Show some of the Cool Ghidra API Functions Belw
- find(Address addr, byte[] values) : Searches memory from ‘addr’ for ‘values’ and returns the address of ‘values’ if it is found
- getBytes(Address addr, int length) : Return ’length’ bytes from memory starting from ‘addr’
- getReferencesto( Address addr) : Get All the XREF’s to addr
- setEOLComment(Address addr, String message): Add an EOLComment at ‘addr’ which has the comment ‘message’
- createBookmark(Addres addr, String category, String note): Creates a NOTE bookmark at ‘addr’
- toAddr(String addressString) : Returns a new address inside the specified program as indicated by the ‘addressString’.
This the just a tip of the iceberg. There so many other Functions in the Ghidra API . Refer this for more details
Here is a Ghidra Script i wrote to Decrypt an XOR encrypted Sring table
| |